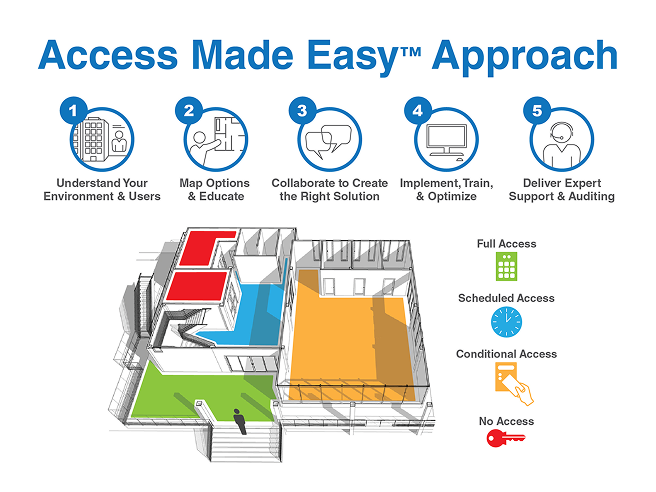
Phase 1: Understand Your Environment & Users
Every organization is different. That’s why we start by listening.
We ask the right questions, observe your environment, and learn how your people interact with your spaces. Whether you’re managing traffic cabinets, retail stockrooms, healthcare facilities, or corporate offices, we take the time to understand:
- Who needs access—and when
- What areas require protection
- What compliance or operational standards apply
- What challenges you’ve faced with past systems
This discovery phase ensures that every recommendation we make is grounded in your real-world needs.
Phase 2: Map Options & Educate
Once we understand your environment, we present clear, tailored options. We believe that knowledge is free, and we’re committed to helping you make informed decisions.
We walk you through:
- Access control technologies (CyberLock, smart card readers, keypads, etc.)
- Software platforms and reporting dashboards
- Integration opportunities with existing systems
- Scalability and future-proofing options
Our goal is to simplify the landscape and help you visualize how smart access can work for your organization.
Phase 3: Collaborate to Create the Right Solution
We don’t believe in one-size-fits-all. Instead, we work side-by-side with you to design a solution that fits your goals, budget, and long-term strategy.
This phase includes:
- Selecting the right hardware and software
- Defining user roles and access levels
- Planning for emergency access and overrides
- Building in flexibility for future enhancements
We bring deep expertise and a diverse toolkit to the table, but we always prioritize your input. Together, we create a solution that’s not just functional—it’s strategic.
Phase 4: Implement, Train & Optimize
Once the plan is in place, we move quickly and meticulously to bring it to life.
Our implementation process is designed to be:
- Seamless – Minimal disruption to your operations
- Precise – Every component installed and configured correctly
- Empowering – Your team is trained and confident from day one
We provide hands-on training, user guides, and ongoing optimization to ensure your system performs at its best. And if something needs adjusting, we’re there to help.
Phase 5: Deliver Expert Support & Auditing
Security isn’t a one-time event—it’s an ongoing commitment. That’s why our support doesn’t end after installation.
We offer:
- Regular system audits
- Access reporting and compliance support
- Troubleshooting and technical assistance
- Recommendations for upgrades and enhancements
Our team is responsive, knowledgeable, and invested in your success. Whether you need help managing users, interpreting audit logs, or expanding your system, we’re just a call away.